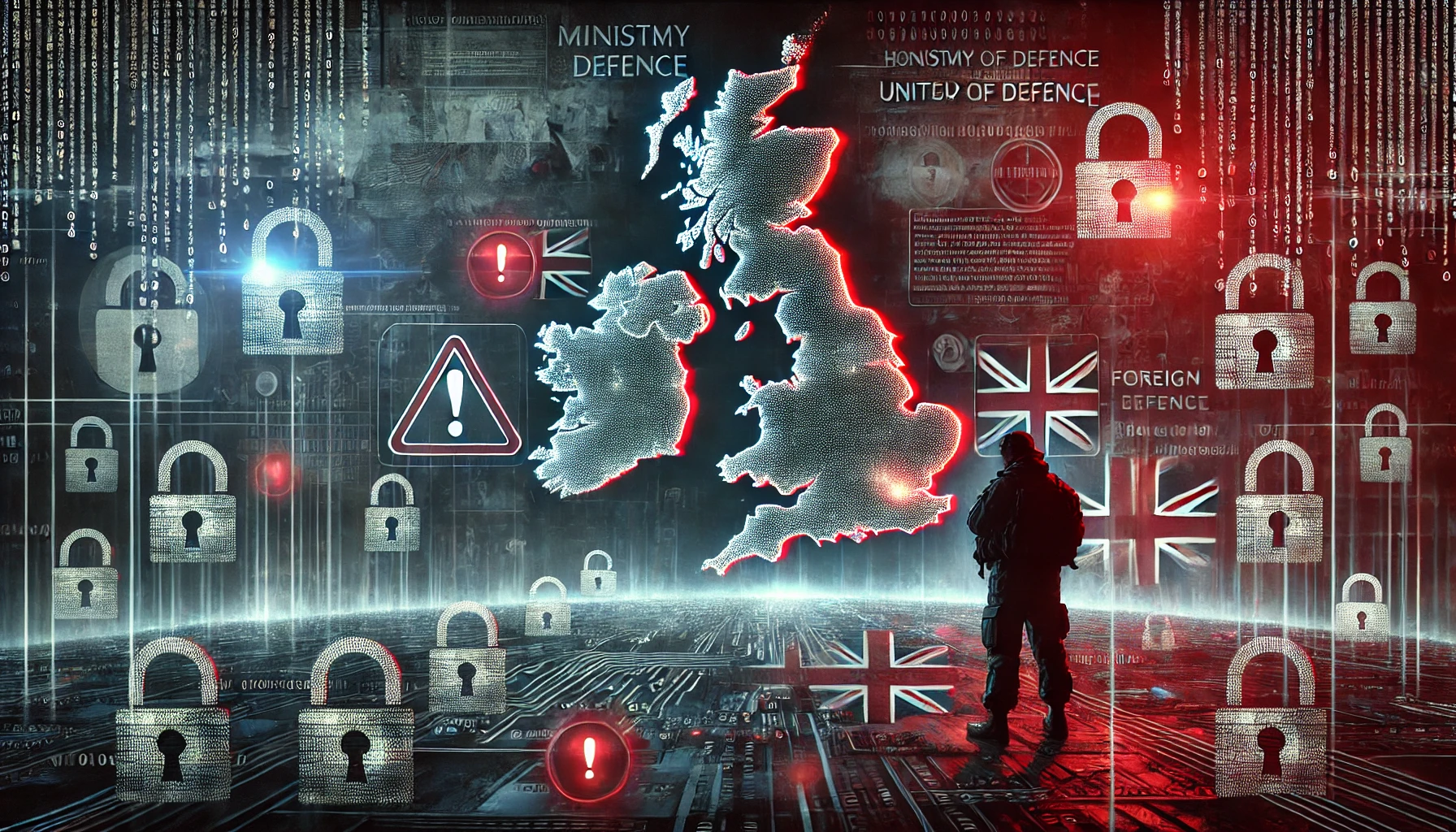
Ah, another day, another cybersecurity breach—and this time, it’s not some private company handling your online shopping data, but the UK’s Ministry of Defence (MoD). Yes, you read that correctly: the very institution responsible for defending the nation has found itself vulnerable to a cyberattack. But before we throw our hands up in despair (or worse, shrug our shoulders in apathy), let’s break down why this breach is more significant than just another blip on the data breach radar.
The Basics of the Breach
Let’s start with what we know so far. The breach came via a third-party payroll system, compromising the personal details of military personnel, including names, bank details, and a handful of home addresses. That’s right: highly sensitive information from individuals serving in the UK’s armed forces has been exposed, leaving them vulnerable to potential identity theft, fraud, and—given their roles—perhaps more sinister activities.
Speculation is rife that a foreign actor could be behind the attack. And while no official confirmation has come from the Ministry, the very fact that this is even a possibility should make every citizen a little uneasy. We’re not just talking about random hackers playing around for fun; this could very well be state-sponsored espionage.
Why Does This Matter?
So, what’s the big deal? After all, data breaches happen all the time, right? Wrong. While it’s true that breaches have become a depressingly regular occurrence, this isn’t a breach of your average corporate entity. This is the MoD we’re talking about—the heart of the UK’s national security apparatus.
A breach like this isn’t just about financial fraud (though that’s bad enough). This is about the exposure of people who are involved in the defence of the nation. These aren’t just private citizens; they are military personnel who may serve in sensitive roles, have access to classified information, or work on critical defence projects. By gaining access to their personal information, bad actors could potentially manipulate or blackmail them, creating security vulnerabilities that could ripple far beyond the individual.
Furthermore, this is a massive reputational blow to the MoD. If they can’t keep their own house in order when it comes to cybersecurity, how can we trust them to safeguard the nation against more complex and dangerous cyber threats?
The Real Issue: Third-Party Vulnerabilities
While the breach may have occurred within a third-party payroll system, the MoD is ultimately responsible for the protection of its data. This brings to light a crucial issue in cybersecurity today: third-party vulnerabilities. In an increasingly interconnected world, organisations—government or otherwise—are relying more on third-party service providers for everything from payroll to cloud storage to software development. And while this can make operations more efficient, it also opens up new avenues for cyberattacks.
The MoD’s breach is a perfect example of how even the most robust internal cybersecurity measures can be undermined by vulnerabilities in external systems. And let’s face it, private contractors don’t always hold themselves to the same rigorous security standards that government agencies (should) do. As the saying goes, you’re only as strong as your weakest link—and when it comes to third-party contractors, that link can be very, very weak indeed.
The Government’s Cybersecurity Track Record
This breach also calls into question the UK government’s overall cybersecurity posture. It wasn’t too long ago that we saw a surge in ransomware attacks across sectors, including healthcare and local government bodies. At the time, we were told that the government would be stepping up its game, investing in cybersecurity to prevent further attacks. Yet, here we are—another critical arm of the state has fallen victim to a cyberattack.
What’s worrying is that this isn’t the first time a government department has been breached, and it certainly won’t be the last. Whether it’s the NHS, local councils, or now the MoD, the UK’s track record on cybersecurity is, frankly, embarrassing. And while we’re assured that “steps are being taken” to mitigate future attacks, there’s little confidence that these measures will be enough, particularly when the government has a tendency to downplay the significance of these events.
The Role of Leadership: Ignoring the Red Flags
This breach raises serious questions about leadership and accountability within the MoD and the government at large. There’s no way that this vulnerability emerged overnight. You can bet that there have been warnings—both internal and external—about the security risks of using third-party contractors for something as critical as payroll services for military personnel.
And yet, here we are, dealing with the consequences of what seems to be a lack of proactive risk management. It makes you wonder: were the warnings ignored at a board level? Was there a conscious decision to take the risk because “it won’t happen to us”? If that’s the case, then heads need to roll. If corporate boards can be held accountable under GDPR for ignoring data protection advice, why should government departments be any different?
The Fallout: What Needs to Happen Next
In the wake of this breach, several things need to happen—and fast. First and foremost, the MoD must launch a full-scale investigation into how this breach occurred, including a detailed audit of its third-party contractors and their security protocols. If the investigation finds that any warnings were ignored or that contractors were not held to high enough standards, there needs to be real accountability.
Second, the UK government needs to revisit its cybersecurity strategy, particularly when it comes to critical national infrastructure. We can’t afford to be complacent, especially with foreign actors eyeing vulnerabilities in our national security systems. Mandatory Cyber Essentials certifications should be a baseline, even for the private contractors handling sensitive government data. And just like in the corporate world, a failure to comply with these standards should come with stiff penalties, GDPR-style.
Finally, let’s not forget about the individuals affected by this breach. Military personnel who have had their personal data compromised must be offered the highest level of support, including identity theft protection services and security briefings on how to mitigate personal risk in the wake of the breach.
Conclusion: A Wake-Up Call We Can’t Afford to Ignore
If the MoD breach teaches us anything, it’s that no organisation—no matter how powerful or well-resourced—is immune to cyberattacks. This is a wake-up call, not just for the Ministry of Defence but for every government department and organisation that handles sensitive data. We need stronger protections, greater accountability, and an acknowledgment that cybersecurity is a national security issue, not just an IT problem.
The question is: will the government listen, or will this be yet another breach swept under the rug, with nothing but vague promises of “lessons learned”? The clock’s ticking. Let’s hope they get it right this time.